“Virtualization” is one of the hottest buzzwords in the IT world today. Virtualizing servers has become a common practice in most large IT shops. We have recently seen the introduction of virtualization with graphics processing cards (GPUs) And of special interest to executives and IT professionals exploring Bring Your Own Device (BYOD) for their business, smart phone virtualization may present a solution to security and privacy concerns.
Even without the intentional practice of BYOD, the flood of personal smart phones and tablets entering the workplace raises many questions about security. Today’s workers demand the flexibility to work not just from employer-provided desktops or laptops, but from personal smart phones and tablets. As these devices encourage out-of-office connectivity, productivity and responsiveness, most companies are loath to discourage such behavior.
But when personal devices are used to access corporate email, applications and data, both the personal privacy demands of the user and the enterprise’s security and control requirements are simultaneously in need of control points and protection measures. The same goes for company provided consumer devices, which end up being used not only for business, but the inevitable access of personal email, data and media.
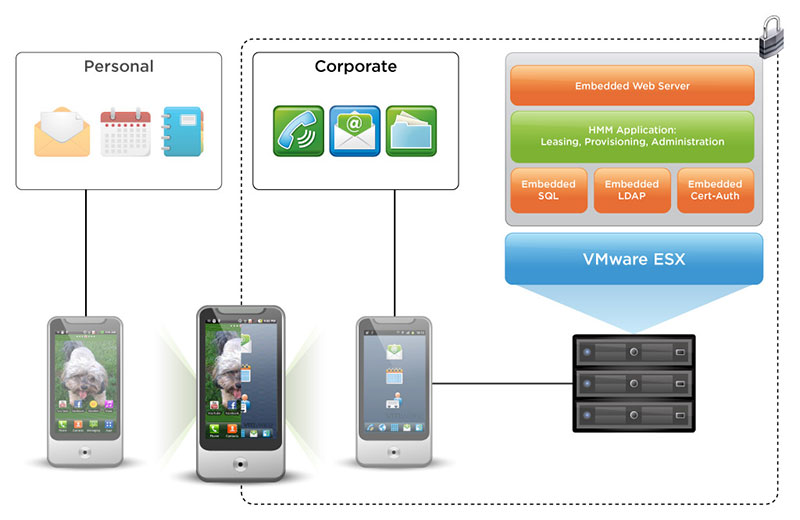
So how to build a wall between the personal and corporate worlds, even when using just one device? Virtualization may hold the key. One of the industry leaders in virtualization, VMWare, has recently unveiled their “MVP” (Mobile Virtualization Platform) that will allow a company to introduce iOS and Android devices securely into the enterprise. The access is controlled via a separate workspace on the mobile device that is entirely controlled by the company. Essentially, personal and business applications and usage are separated.
The user of a mobile device MVP-enabled now has 2 personas: Personal and business. The user can toggle between the personas and isolate one of the identities in a secure fashion. Companies have full-control of the mobile workspace, including VPN, authentication, encryption and directory services. Corporate IT controls all aspects of the device lifecycle for the corporate persona.
Logging into the business portion on such a device serves up a secure workspace with the applications, data and files used during the workday. The smart phone is temporary locked in work-only functionality, one that could be served by a different network than the phone owner’s service provider. Once the employee logs off, access to proprietary company data is no longer available, nor can they access non-work related apps (think Facebook) while in the professional workspace.
This class of technology is in its infancy, but the demand for secure control of the ubiquitous mobile device as it enters the workplace is growing and will surely become a common technology for most enterprises. Both companies and employees see obvious benefits from such an approach, making smart phone virtualization an obvious win-win.


